Phishing Campaign Delivering Three Fileless Malware: AveMariaRAT / BitRAT / PandoraHVNC – Part II | FortiGuard Labs
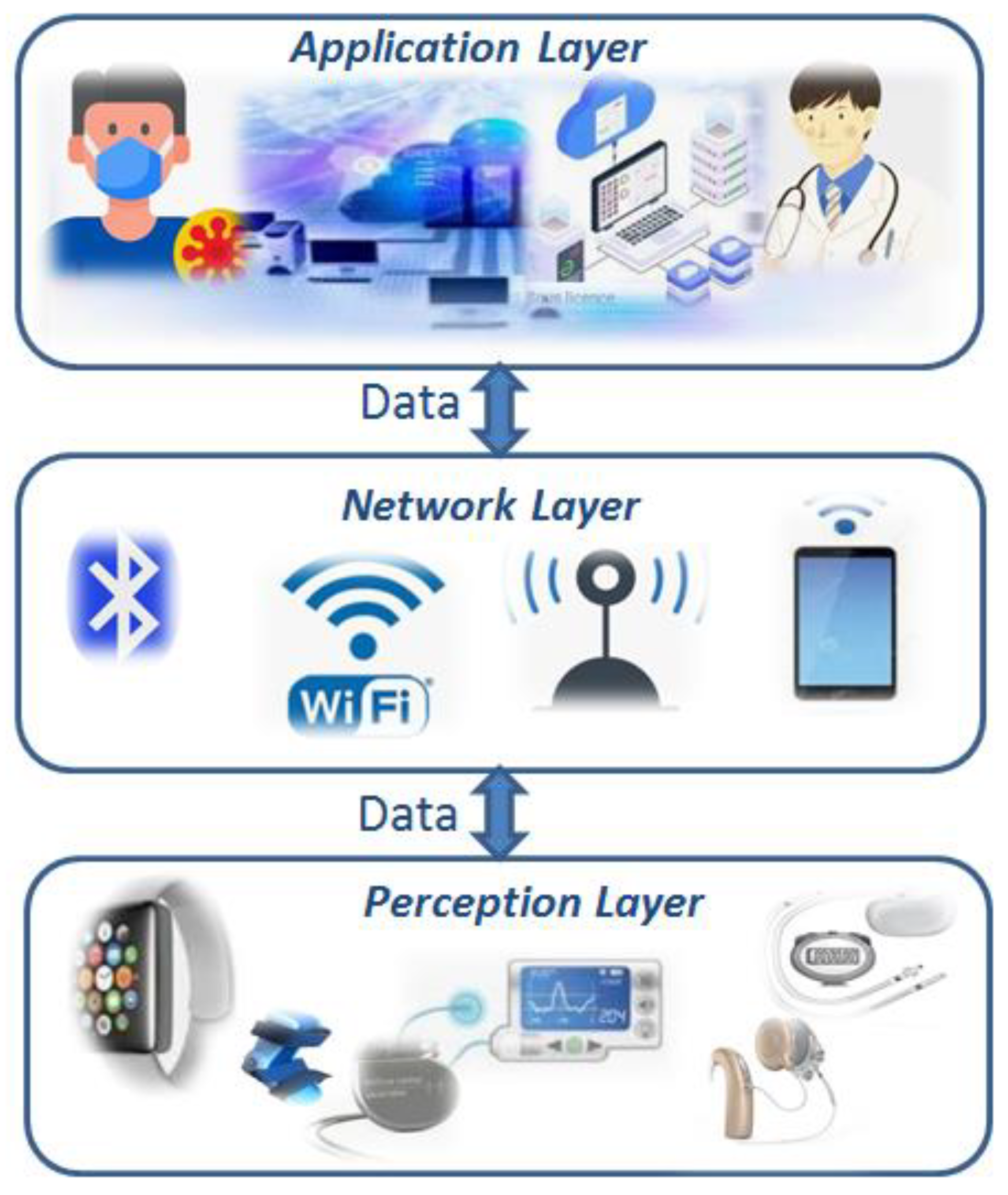
JCP | Free Full-Text | Security and Privacy Management in Internet of Medical Things (IoMT): A Synthesis
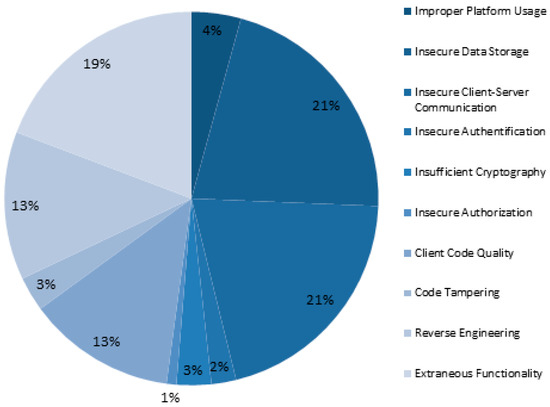
Systems | Free Full-Text | Identifying the Mutual Correlations and Evaluating the Weights of Factors and Consequences of Mobile Application Insecurity
/cloudfront-eu-central-1.images.arcpublishing.com/prisa/NJMN7WDH3ZBTBAKBULAYPJPVEQ.jpg)
Pandora Papers: Catalan Popular Party mayor was linked to a firm created in a tax haven | Spain | EL PAÍS English